This article reminds me of an incident from my past life. I used to work for a Fintech company that was also into PrePaid Instrument wallets, powering one of the biggest utility service providers in India.
One day while doing an Attack Surface Management exercise, something strange happened. I noticed that our company name was quite popular on Youtube and associated hashtags were “free Netflix trial”, #freenetflix. This was around the time Netflix had entered India.
Attack Surface Management (ASM) is basically trying to find out all the references and entry points into an organisation’s servers / apps/ IPs on the web. This is done by doing deep searches using google dorks, dark web/deep web in both manual and automated ways. Nowadays, there are third-party companies that specialise in these.
Trivia: Interestingly, Cyber Insurance companies also use these ASM techniques to understand more about their clients digital footprint, exposure etc., and use it for calculating Cyber Insurance Premiums.
Curious, I dug deeper and found out a youtube video where an influencer had put up a tutorial on how one could easily create a virtual prepaid card in our platform, loading it for INR 2/- and then use that for Netflix trial for about a month and then recycle the whole process. I figured out that:
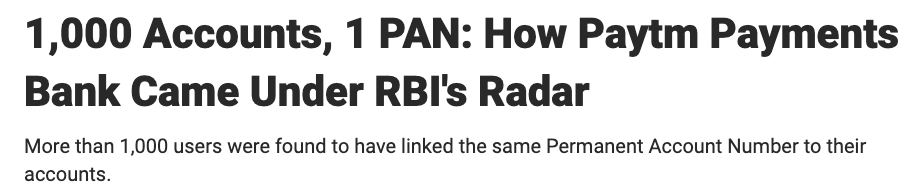
They were using the same Driving License (DL) numbers and sometimes recycling DL numbers by appending a digit. Since, in Minimum KYCs only numbers and some basic details like name and etc were collected, usually without any kind of photocopy of the documents. I believe this process has improved now (?).
I took those details and with the help of the internal teams, started researching more about those DL numbers. Turns out there were close to a few hundred accounts associated with that single number. Ideally, the systems should have flagged and blocked subsequent wallet creation using the same ID numbers. Somehow it was failing.
We looped in Compliance, FRM and legal. Such accounts with dubious credentials were invalidated and we started rolling out additional controls.
It was trivial to use the same numbers, unless there was a robust mechanism that checked the Document ID numbers and the associated identifiers like Mobile number, names etc.
Though I was in cybersecurity, this was my first brush with fighting digital fraud.
In another incident, fraudsters had cloned our fintech app and we had to loop in our legal teams to send a Trademark infringement to the AppStore to get this fake loan app removed.
In security we analyse the Tactics, Techniques and Procedures (TTPs) that are used commonly by the hackers. This helps us security teams in detecting and mitigating attacks by understanding the way threat actors operate.
Adapting a similar approach of examining the tactics, techniques, and procedures used by fraudsters will provide valuable insights into their behaviour and motives. With this understanding, the Fintechs and FIIs can help develop effective countermeasures. A good start would be documenting all the counter-fraud use-cases !
A key takeaway or a piece of advice to all the fintechs is to build a comprehensive list of use-cases proactively, and have them tested thoroughly. You can take help from your InfoSec teams in building these use-cases!
What do you say ?
#DigitalFraudPrevention #fintech #fintechfraud #search #attacksurface #TTPs #Tactics #Techniques #Procedures #usecase #ThreatActorAnalysis #frauddetection