The lockdown has forced people to look and feel differently. While the fashion of beard still continues to rule, ponytails and long hairs are not so much in the vogue these days. Quite a few people have asked me how do I manage to shave my head. Yes, I do it myself and what started off in 2015, is now a monthly or weekly routine.
Hoping this will help all you people who are on the fence whether to give their heads a cleanup either with the help of a barber, partner or all by themselves.
Shaving the head is not for the faint-hearted and Very few people understand the change a bald head brings about. It’s a process, it’s a journey to lose one’s identity. No wonder the first thing many criminals do after a crime is to shave their head 🙂 or at least that’s what I have read and understood from reading the news paper reports.
Jokes apart, it’s a tedious process to get rid of the hairs on your head, especially if you are going to do yourself. The first time I decided to let go of the hair, it was by myself. There were lot of thoughts on what would others say especially the family, friends and colleagues who will pose a zillions of questions ! More importantly what would you say to yourself ? The moment I got the courage and calmness to accept, rest of the process was just technical.
Here are few things that you should know before embarking on this journey:
- It’s a time consuming process, you need to be patient and willing to spend some time
- You must invest in right tools
- Be ready to clean up the mess!
- Face the consequences (including funny faces from young and old, get questioned on why? )
Prerequisites:
- A good trimmer
- Good razor
- Shaving foam & an aftershave
- Towel
- Mirror(s)
- Old newspaper/waste papers
Preparation:
Shaving your head takes a good amount of time and it’s not something you can do on a daily basis. It can take anywhere between 20–60 minutes depending on which part of the learning curve you are. Its best done when you are relaxed and have sufficient time in hand. I prefer weekends when I don’t have to rush into any meetings. And this is the time you will need to invest every time you want to shave your head.
You do not start off by trying to shave with a razor directly. That would be disaster in the making. Buy yourself a good hair-trimmer, I was using a Panasonic trimmer for close to 10 years until the battery died. I even dismantled and got it working with a standalone battery but I screwed up while putting the covers back and broke a tiny hinge.

A trimmer is an engineering marvel, so many tiny parts working in such harmony. Unfortunately here in India it is not easy to get the original replacement blades and you might as well pick a new trimmer instead of trying to source the replacement items for the same price!
The choice of trimmers is yours: Corded or battery operated, and each one has its own pros and cons. Corded ones are usually powerful and trim the hairs faster and better. But if you live in a household where there is frequent power-cuts I suggest buying a trimmer that also provides battery.
I currently use this which supports both corded and cordless operation, it has a battery backup as well.

A big and a good mirror is beneficial, bonus points if you have a smaller hand held mirror that will come in handy to see the back of your head.
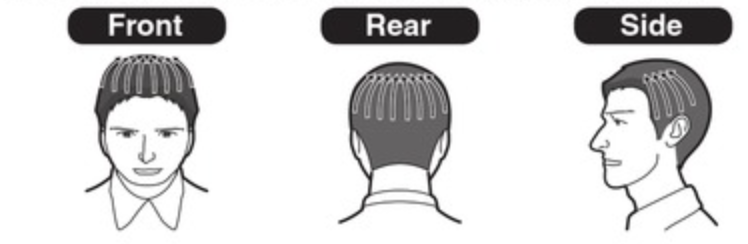
You can move the trimmer as shown above.
I would advise putting a newspaper on the top of the sink (make sure there are no traces of water and its dry) and putting all the cut hair onto it directly. There’s a trick on how to do it. Using a trimmer start from the back of the head (as shown in the pic) and move it slowly till it reaches forehead. After every stroke make sure you clean the blades with a brush. You can bend and drop the cut hairs directly onto the newspaper . Repeat the process multiple times to shave all the hair. Be careful when you shave the hair behind your ears as you move the trimmer, chances are you might get a cut. Once you have shaved fully its good enough for a stubbly look or you can proceed further to shave using a razor for a smooth finish. If you intend to shave, I strongly suggest using a shaving foam instead of gel or cream as its easier. Buy a good brand of foam, after all its your head.
For the razor I have used Schick till the blades ran out and now have settled down with Gillete Mach-3. I have never bothered with the pro-glide or razors with n number of blades 🙂 I also tried with a foil shaver but its not good for the head.
Paste the foam all over your head and give it a minute to settle down and then like the trimmer, start from the back of the head and all the way till forehead. Rinse the blades generously. I use a mug of water with a few drops of dettol. Be careful when shaving behind ears, be slow otherise the sharp blades can result in small cuts on ears. Once done with the shaving I use aftershave / balm. No preference, use the one you are comfortable with, but do dab few drops and not take the shower directly after a shave.
Now comes the hard part. If you love a hot shower like I do, lower the temperature or keep it luke warm as your head now no longer has the cushion of hairs otherwise the hotness will hit you.
Take a look at your bald head in the mirror and savour it. You will find a new in you.

You are vulnerable
All seasons are harsh on the bald head. In summer the sunlight is intense, while in winters the chill hits your head. I had a tough time at the office sitting in an Air-Conditioned environment and you will find it colder than usual so much that, you may catch sinus. Invest in good hats, caps and scarfs, baclavas or even the neck warmers. Same is if you commute in metro trains where the temperature is much colder (especially Bengaluru Metro).
I now have close to 5 caps and an equal number of scarves. Go on and show off the fashionista in you. Nights are harsher than days and usually wrap my head with a scarf while sleeping for atleast the first 1–2 nights, otherwise the next morning will have a runny nose. If you exercise regularly, buy few headbands or scarves as there are no hairs to hold off the sweat.
Be ready to be the center of attraction and also some pun, especially when surrounded by the kids. India is not kind to bald men. People make fun of you, stereotype you as motte, taklu, boda and what not. Even there are some religious restrictions that you cannot shave heads…
Anyways, now that you have let go of your hair, enjoy everything that comes with it…I no longer have to worry about carrying a comb, not worry about the shampoo or the conditioner, take headbath only twice a week etc
Smile when you bump into a bald head, next time.