Today, this email landed in my inbox stating that one of the hosting accounts at Bluehost would soon be de-activated as it contained excess directories! As it landed in the inbox instead of the spam folder, it had already breached the first line of defense, the usually reliable Google spam and anti-phishing filters.
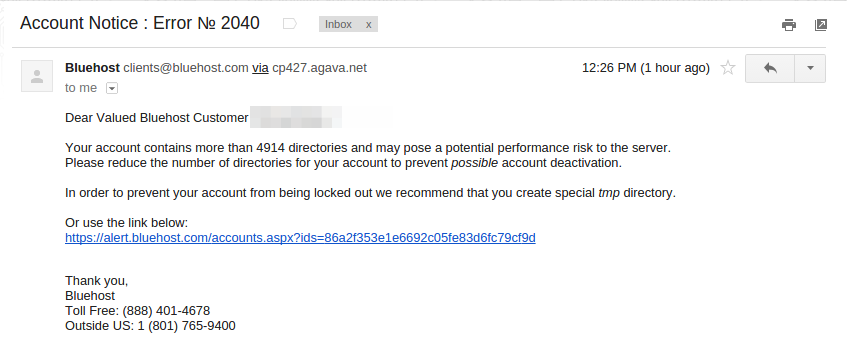
Unlike the other phishing emails that generally target the users on retrieving banking details and are usually written with poor grammar, this one looks a little sophisticated and is closer to a spear phishing campaign. The message makes use of custom fields, like addressing the users with Firstname Lastname, content is cleverly framed as it talks about the potential performance risk to the server and also makes use of clever formatting of the text. Notice how the word “Possible” is italicized to drive a point, though it got me wondering on how creating tmp folders could improve the performance!! Also, I am wondering as to from where the user account database may have been leaked(?)
Text Content of the mail:
"Dear Valued Bluehost Customer <Firstname lastname>
Your account contains more than 4914 directories and may pose a potential performance risk to the server. Please reduce the number of directories for your account to prevent possible account deactivation.
In order to prevent your account from being locked out we recommend that you create special tmp directory.
Or use the link below: <Link>
Thank you,
Bluehost Toll Free: (888) 401-4678
Outside US: 1 (801) 765-9400"
This is how the linked web-page looks like. Note the actual URL:
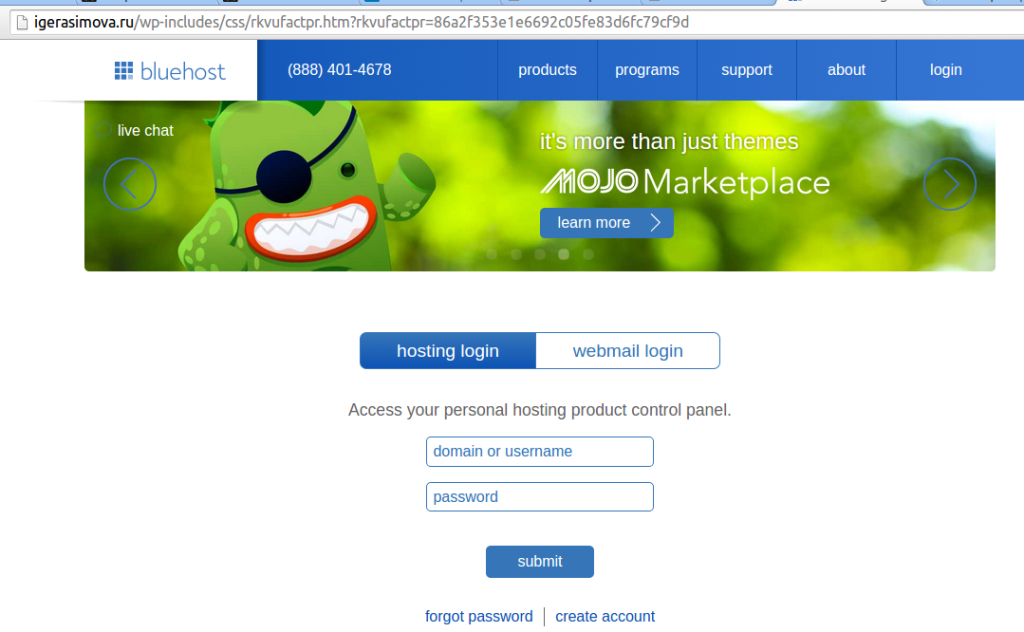
bluehost-spear-phishing-webpage
Mail Headers:
Return-Path: <nouikip6@cp427.agava.net>
Received: from cp427.agava.net (cp427.agava.net. [80.78.250.93])
by mx.google.com with ESMTPS id et1si5436672lac.11.2015.05.23.23.56.37
for <<actual email>>
(version=TLSv1.2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Sat, 23 May 2015 23:56:37 -0700 (PDT)
Received-SPF: pass (google.com: best guess record for domain of nouikip6@cp427.agava.net designates 80.78.250.93 as permitted sender) client-ip=80.78.250.93;
Authentication-Results: mx.google.com;
spf=pass (google.com: best guess record for domain of nouikip6@cp427.agava.net designates 80.78.250.93 as permitted sender) smtp.mail=nouikip6@cp427.agava.net
Received: from nouikip6 by cp427.agava.net with local (Exim 4.85)
(envelope-from <nouikip6@cp427.agava.net>)
id 1YwPps-0026cH-S1
X-PHP-Script: www.nouikip.ru/includes/w2.php for 91.223.123.43, 91.223.123.43
A reason this may have got through Anti-Spam-Phishing filters could be because the mail servers used to send the message have passed the Sender Policy Framework (SPF) checks and are designated as permitted senders.
Also, from the above headers it is clear that this mail was sent using a Form hosted on the IP/site listed in X-PHP-Script. Screen-shot of this page looks as below. It may be that the site below is deliberately insecure or a probable mis-configuration allowing others to leverage it (?)
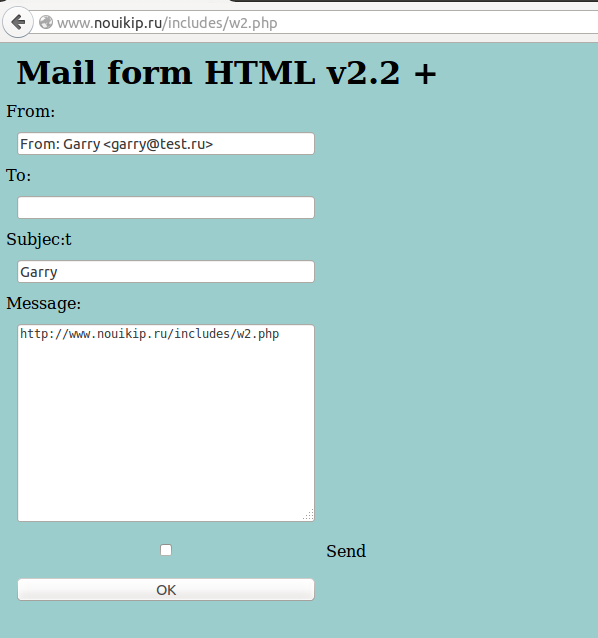
spear-phishing-targetting-using-php-script
I usually do not look into such messages if they land in the spam folder, this is an exception as it landed in my inbox passing through the spam filters and with an interesting scenario.


