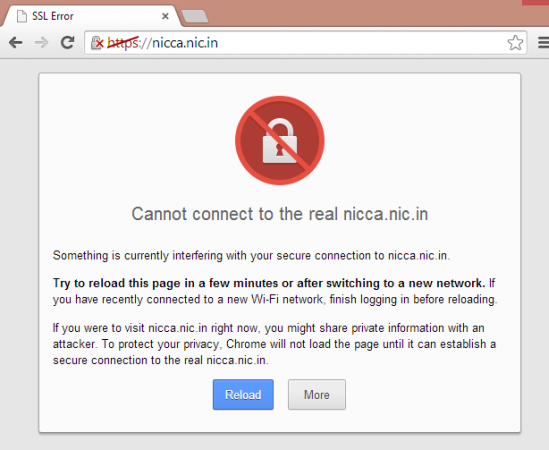
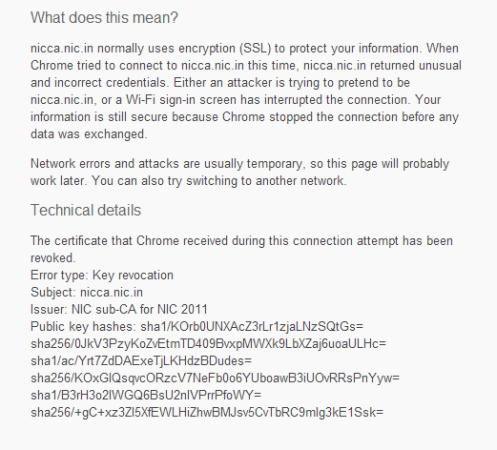
If you are filling up the online form at Passport Office’s website for a new passport or for renewal, please pay close attention to the last field before the Submit Button.
One of the option there states that:
“I authorize Passport Seva to share my name and contact with companies that offer financial, travel & tourism products, where such companies may offer special schemes for passport applicants from time to time. With my consent as YES, i agree to override the Do-Not-Call (DNC) mandate for the communication I may receive from them“
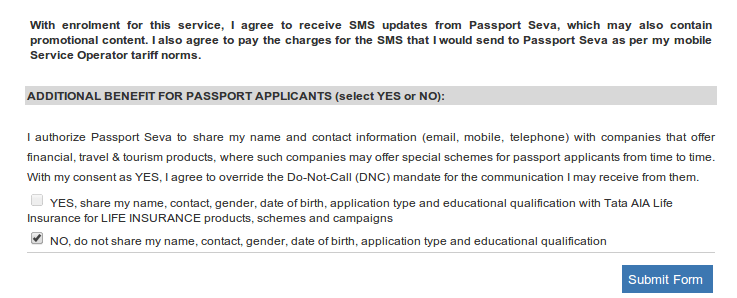
While the check box has further information on what information is shared: “YES, share my name, contact, gender, date of birth, application type and education qualifications with <the advertiser/third-party service provider changes with the time, check the screenshots below>”
In my opinion, this is a bad feature and am very apprehensive of the fact that Passport office provides an option to share our personal information with Third Party providers. I am wondering who gave them the idea to monetize on our private information, of course this is a opt-in but still. What more that the list of Vendors changes with the time. I had taken the screenshot a few months back and again revisited the page to check, but this time it showed a different service provider! Once these information is shared, we do not have any control on how it is stored and used. My recommendation to Passport Office is to stop sharing these information at the earliest, with or without choice, and if you are filling the form, ensure you select Do Not Share option.
The below screenshot was taken few months back, it was TATA AIG for Life Insurance then:
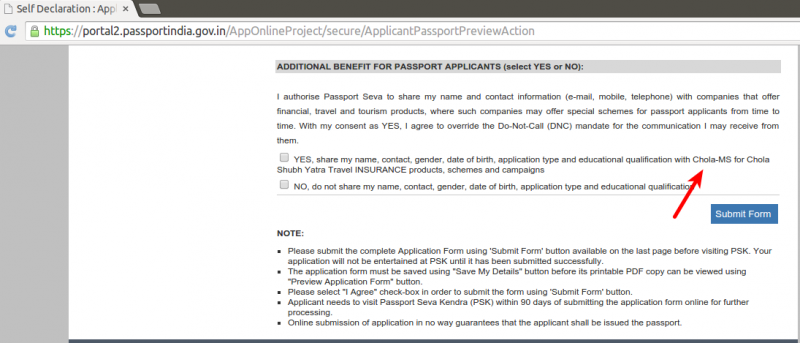
Currently the vendor is listed as Chola-MS for Chola Shubh Yatra Travel Insurance:
I tried giving feedback at the passport office site here. But there is no way to proceed unless one provides the file number and other details!